What is OSINT? 5 Best Open Source Intelligence Tools

When it comes to intelligence, the best things in life really are free - or at least, very low cost. Open source intelligence (OSINT) is a legal and accessible way of gaining intelligence of all kinds. Conducted properly, businesses can use it as a low-cost way of gaining significant advantage - and many of the best OSINT tools are freely downloadable.
What is OSINT?
The intelligence community, one of the heaviest users of open source intelligence, defines it as intelligence derived from publicly available sources to target a specific intelligence requirement. Most of this information can be obtained for free, although some comes from low-cost paid lookup services including people directories and public business records.
Why do businesses need open source intelligence?
Businesses can use OSINT for tasks ranging from tactical investigations with wide-reaching ramifications through to practical short-term projects. On the tactical side, a company could monitor developing events in a specific market to build intelligence about the practicality of doing business there. Alternatively, it could use OSINT tools to map out all online properties belonging to another company as a way of assessing its international operations. It can also use open source intelligence techniques to investigate the source and perpetrator of a cyberattack against its own systems.
Shorter-term open source intelligence projects can include investigating partners and potential clients, looking into a company's prospects, or the reliability of key staff. A company could use it to conduct its own vetting for job candidates, especially for key positions that demand more than a regular background check.
Open source intelligence tools doesn't have to resemble CIA trade craft. Something as simple as Hunter's TechLookup service is perfect for understanding what technology a company uses internally, which can be a valuable clue when identifying potential sales prospects.
Then, Domain Search can help to find the right person's contact details within the target company based on domain names you collected.
OSINT tactics
OSINT is a powerful process that can generate impressive results, but how do you do it? Here is a useful series of steps that apply regardless of your goal:
1. Define your question
To launch an effective OSINT campaign, you need a clear motive. This can reflect specific short-term questions such as "what are the email addresses of the target company's board members?" It can be broader, such as "what are the professional backgrounds and personal hobbies of the board members that we’re about to begin negotiations with, so that we can gain more traction with them?" Or it can be open-ended, such as "Provide ongoing information about business opportunities within the target country’s public sector."
2. Define investigation data points
The information gathering process begins by identifying the information you want to discover more about. This will usually crystallise into data points ranging from names and phone numbers to online user names, email addresses, domains and IP addresses. Depending on the scope of your investigation, these data lists can get pretty long.
This stage is iterative. Your list of data points will grow as you discover more information, and you'll refresh it repeatedly as you work through subsequent steps.
3. Use information sources to search for information
This is where the real work begins. Use the data points to search across available information sources. There is a huge list to choose from, including obvious ones like search engines and social media sites, but also others including public records and online databases.
The nature of your investigation will help you to narrow this list down and provide a basic starting point. For example, certain types of investigation lend themselves to company reports, conference proceedings, and NGO publications. Others might call for extensive mapping work.
It's worth noting here just how much the web has changed the OSINT landscape. Not only did it create more OSINT tools for researchers to use, but it also created a whole new layer of digital information. Companies and individuals who participate online at all create a kind of digital exhaust trail that didn't exist. Now, they have email addresses, domains, and IP addresses. These data points can all be searched and cross-referenced.
The key skill in this step is pivoting. Searching on one data point such as a user name might turn up new data points, which in turn spark their own searches. Consequently this step is worthy of a book in its own right, as the search procedures are extensive and complex. Michael Bazzell has created some flowcharts for OSINT searching in his excellent book on the topic. While he has updated these to reflect best OSINT tools and techniques, some useful older versions can still be found online.
4. Collect and collate data
The ocean of data that you collect will quickly become overwhelming. Have a place to catalogue it so that you can quickly refer back to it. This is important not just for remembering what you've found; preserving your findings will also be useful should they disappear from the web. Ideally, this information should be searchable, and you should have a way to document the relationships between different assets.
5. Analyse information to answer your questions
The final step closes the circle, answering your original question by distilling useful intelligence from the data that you've gathered. Sometimes the data points you retrieve - such as an email address you were looking for - will represent that answer directly. Other answers might take more analysis and inference.
OSINT tools
There is a constellation of available tools targeting these different steps. Below are some of our favourite and most popular OSINT tools for each step in the OSINT process.
Defining data points
We'd be remiss not to mention our own tools at Hunter here. The Domain Search makes it easy to retrieve email addresses for people at specific domains, which can be valuable data points for further investigation.
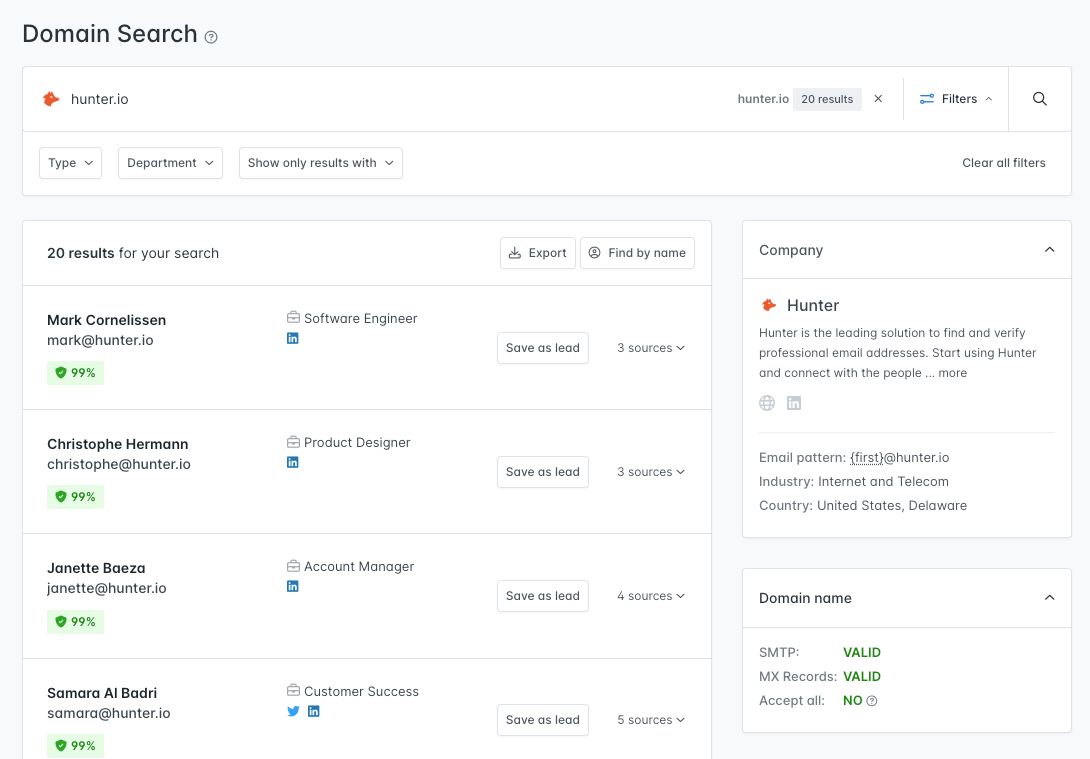
This is also available as a module in the Spiderfoot automation OSINT tool, which is like a Swiss Army knife for open source intelligence investigations.
Search
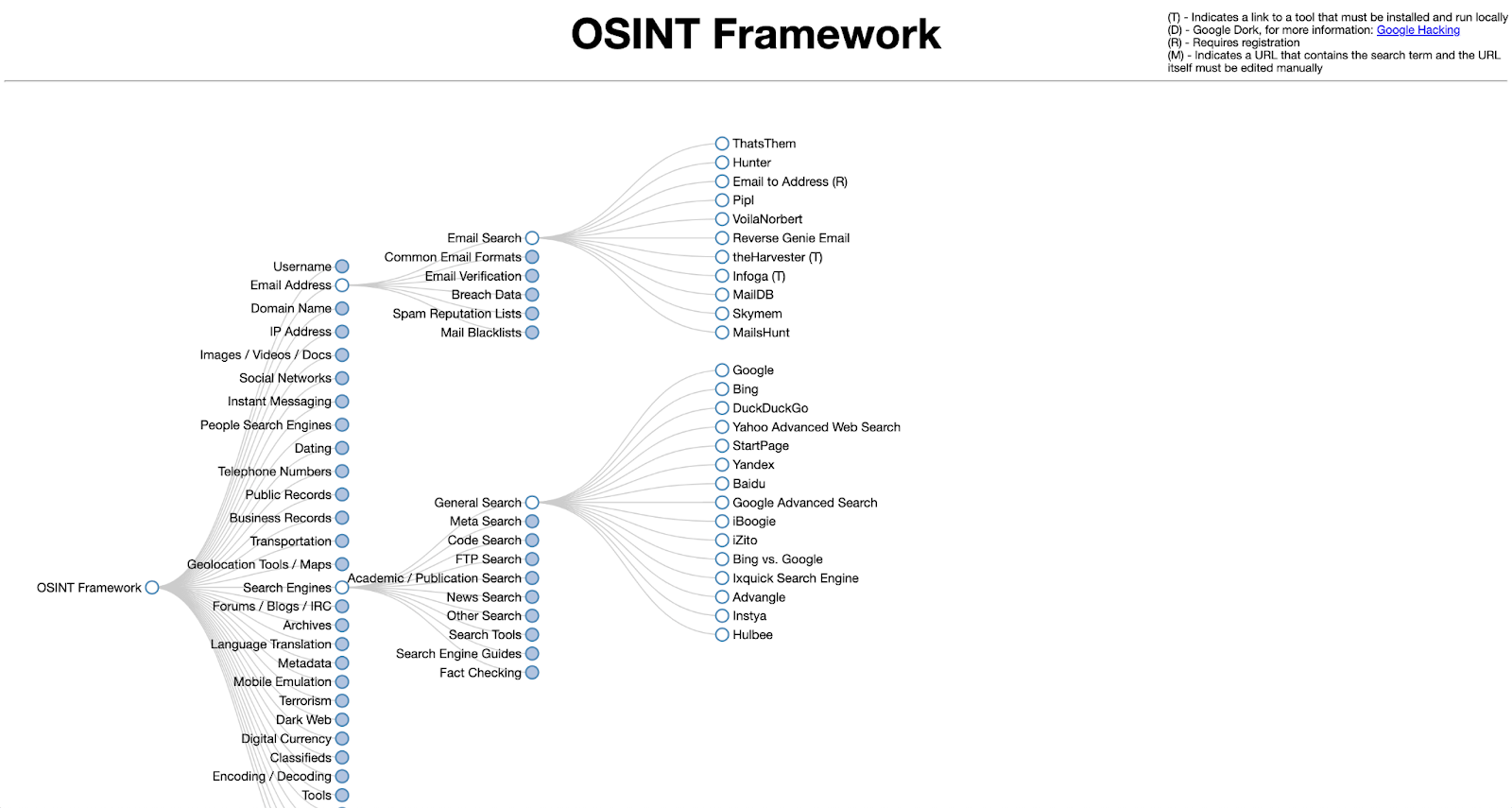
There are so many tools to use here that we can't list them all (Google would definitely be the most well-known OSINT search engine example). However, the OSINT Framework website is an easily navigable collection of links to tools for:
- Business records databases
- Classified advertising searches
- Dating sites
- Domain name mining
- Forum and blog searches
- Geolocation data tools
- People searches
- Public data records
- Social media forensics tools
- Transportation record searches
- Username search engines that scour different online accounts for a single account handle
Don't restrict searches purely to online search engines. You can also mine digital files for data. One category on the OSINT framework explores tools that help you to extract embedded metadata from documents including images. We like Sherloq, an open-source forensic toolset for images, which runs locally on your system. It can derive metadata showing the time that a photo was taken, the device used to take it, and even in some cases the location of the photo. The tool can even show this on a world map.
Information gathering and collation
The OSIRT browser is a free OSINT documenting browser with an in-built search engine designed to help you save online findings as you go.
Analysis
Maltego offers its Casefile and Maltego OSINT tools for analysis. The former is an OSINT tool for documenting evidence in an OSINT investigation while also analysing relationships between entities. Maltego takes this to the next level, with search engine for online information about individuals and other entities.
OSINT research can be as simple as an email lookup or as complex as a multi-month investigation spanning dozens of countries and hundreds of public data sources. For some examples of more complex investigations, check out Bellingcat, the nonprofit OSINT investigation group that goes into detail about how it investigates geopolitical incidents.
As a business, your own OSINT activities are unlikely to get that complex. Nevertheless, even a smattering of skills in this area can net you a competitive advantage for minimal investment. It's also an enjoyable pastime that flexes your intellect - and delivers the ultimate in job satisfaction when you find what you're looking for.




 Send cold emails with Hunter
Send cold emails with Hunter